Project Title
CARAMEL: Artificial Intelligence based cybersecurity for connected and automated vehicles
Project Information
CARAMEL aims to assess the security vulnerabilities at modern vehicles, by using novel artificial intelligence and deep learning techniques for anomaly detection. In addition, CARAMEL will study attacks specially designed to confuse vehicle neural network classifiers. More specifically, the autopilots required for autonomous vehicles are heavily dependent on computer vision and AI techniques. Neural network methods teaches vehicles how to act in particular situations based on what is being detected.
The potential for cyberattack here arises when images are intentionally manipulated in a way that a human recognises them correctly, but a neural network or computer vision-based system misclassifies them. The use of such images opens a way to new attacks on autonomous vehicles, requiring non-conventional cybersecurity techniques to detect and possibly mitigate. Moreover, these attacks do not require any physical access to the vehicle or tampering with the communication system and the consequences of such attacks can be severe.
0 infinity contribution
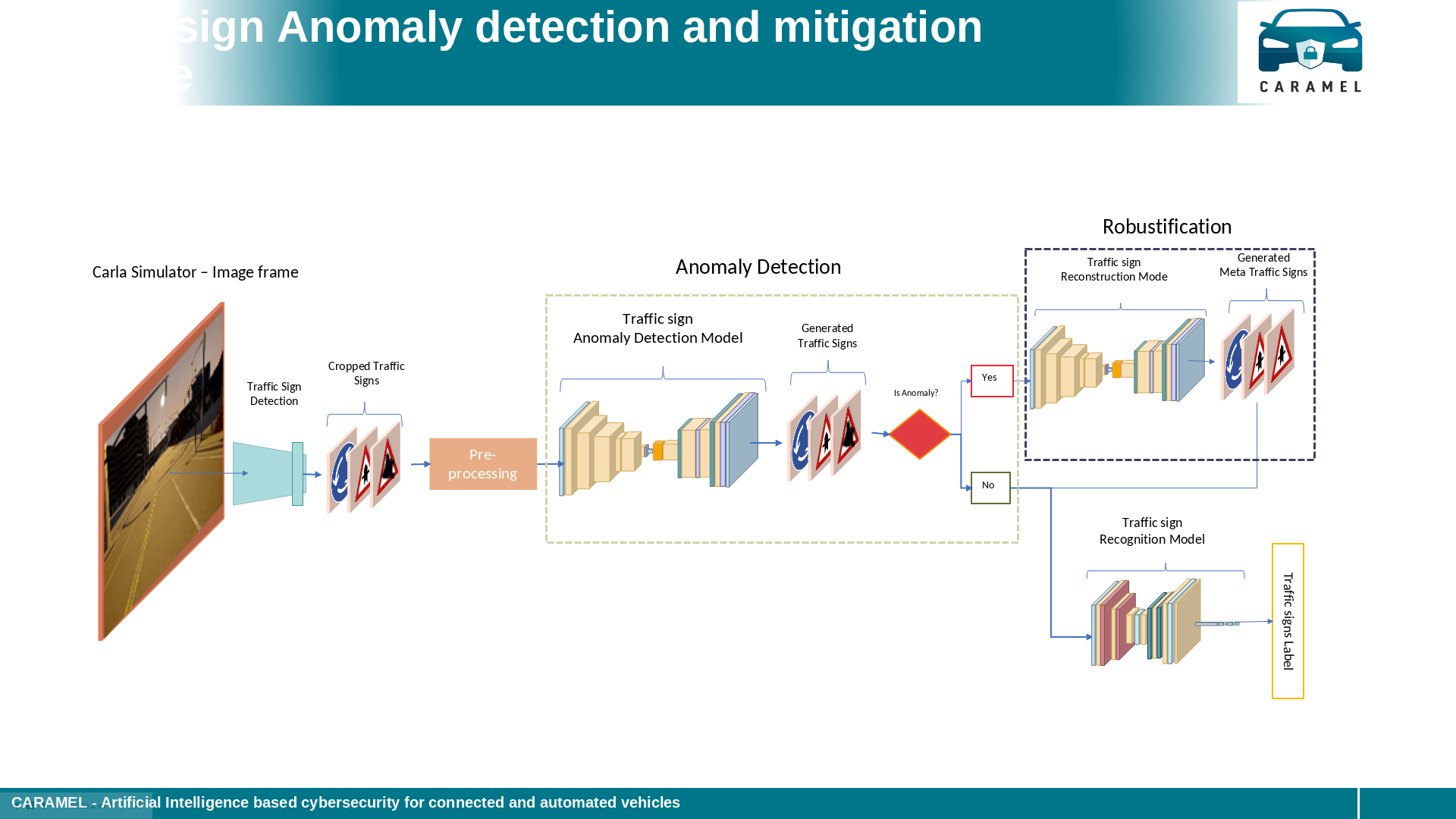
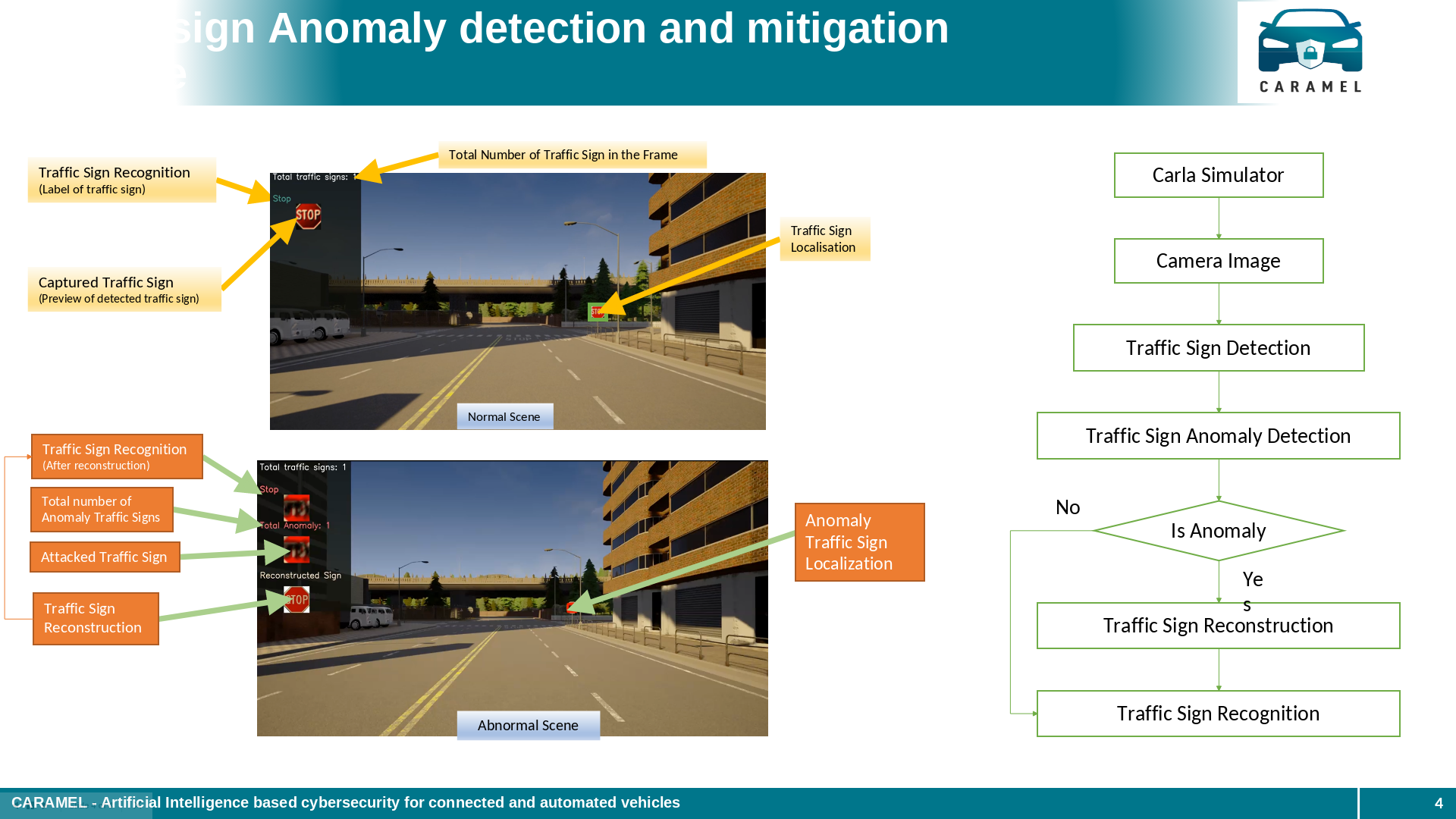
As a result of the CARAMEL project a new pipeline with novel deep learning models for traffic sign anomaly detection in real time were developed. Robust models based on novel deep learning architectures were designed and trained to recognise these types of attacks by improving the training process including data of cyberattack cases, considering deep neural networks for anomaly detection and classification mechanisms of the observed data to real or fake, and data augmentation and generation including cyberattacks for training using novel generative adversarial networks (GANs). These models are able to detect alterations on traffic signs that performed on purpose aiming to mislead the vehicles, and then reconstruct the original ones avoiding erroneous recognitions. The developed methods were integrated into an embedded device that can be part of the autonomous vehicles. Also, the solutions were tested in real and simulated environments and a database with attacked data was collected. Finally, our team has published a science paper (see references) with two more due.
Traffic sign anomaly detection and mitigation pipeline
Technical Achievements